Communication in the out-of-the-box Thorntail service is carried over HTTP. However, the world tries to move to HTTPS to embrace security, which means sometimes, even for a development, HTTP is not enough. For example, Swagger UI, one of the Thorntail’s fractions, for “Try it out” creates API endpoints URLs with HTTPS protocol, even if the service is served over HTTP.
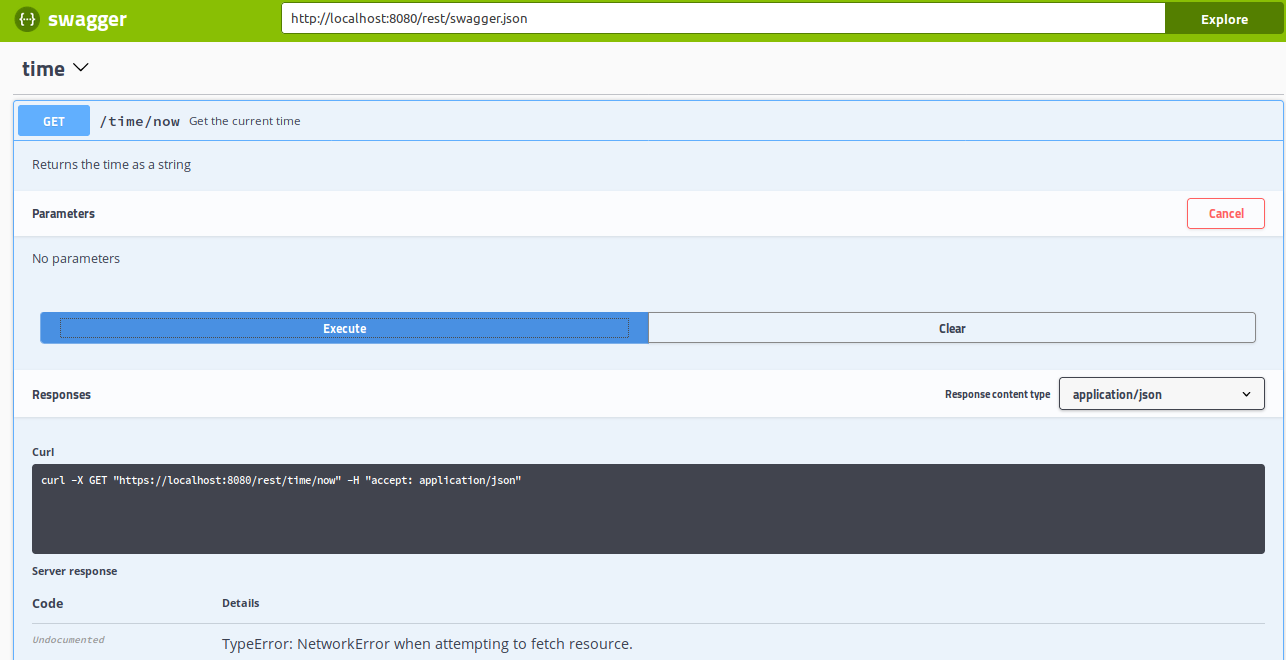 Example of HTTPS link created for HTTP service by Swagger UI
Example of HTTPS link created for HTTP service by Swagger UI
But the main reason for enabling HTTPS should be the security of service users. By no means, I am a security expert, but setting up HTTPS should be a minimum requirement from each web service.
Enabling HTTPS in Thorntail
Reverse proxy HTTPS traffic to HTTP service.
In production, I would recommend using Cetrbot to automate certificate issuance from letsencrypt.org free Certificate Authority (CA), and a proxy server (for example Nginx) to reverse proxy HTTPS traffic into HTTP service.
Configure Thorntail to use Java Keystore
I recommend the above solution as it allows to automate the process of renewing SSL certificates. However, if you are using CA other than Let’s Encrypt, or you already have a certificate, then Thorntail can be configured to use Java Keystore. These stackoverflow question and blog post from Oracle give instructions on how to generate a keystore from an existing certificate.
Having keystore, we need to configure a Thorntail service to use it. It can be done in 2 simple steps described below.
1. Add keystore configuration to a service configuration file.
To configure a Thorntail service to use a keystore a following configuration needs to be added to project-defaults.yml file
thorntail:
https:
keystore:
path: <path_to_keystore_file>
password: <password>By default the service is configured to listen for HTTPS traffic on a port 8443. This can be changed by adding thorntail.https.port config:
thorntail:
https:
keystore:
path: <path_to_keystore_file>
password: <password>
port: <https_port>2. Add management fraction to the service.
HTTPS listener is only enabled after management fraction is added to the project (and I’ve learned it the hard way :)). In the Maven project, fractions are added as project dependencies in pom.xml file:
<dependency>
<groupId>io.thorntail</groupId>
<artifactId>management</artifactId>
</dependency>The version of the dependency is configured in Thorntail-bom, which should be added in dependencyManagement section of pom file, if project has been created with Thorntail Project Generator.
Auto generate a self-signed certificate
Above 2 solutions might be an overkill for a local development though. In that case, Thorntail can be configured to auto-generate a self-signed certificate
thorntail:
https:
certificate:
generate: true
port: <https_port>Just to remember that the Undertow fraction must be added to the project (same as in the keystore solution above).